-
Using the HTTP Strict Transport Security (HSTS) response header
To enable the HTTP Strict Transport Security (HSTS) response header. Open the settings.yml file located in the Arc installation directory and add the following parameter:
-
Using TLS protocols v1.2+ with Arc
To enable Arc to use only TLS protocols (v1.2+) and ciphers that are known to be secure:
-
How to activate auto-save processes in Arc
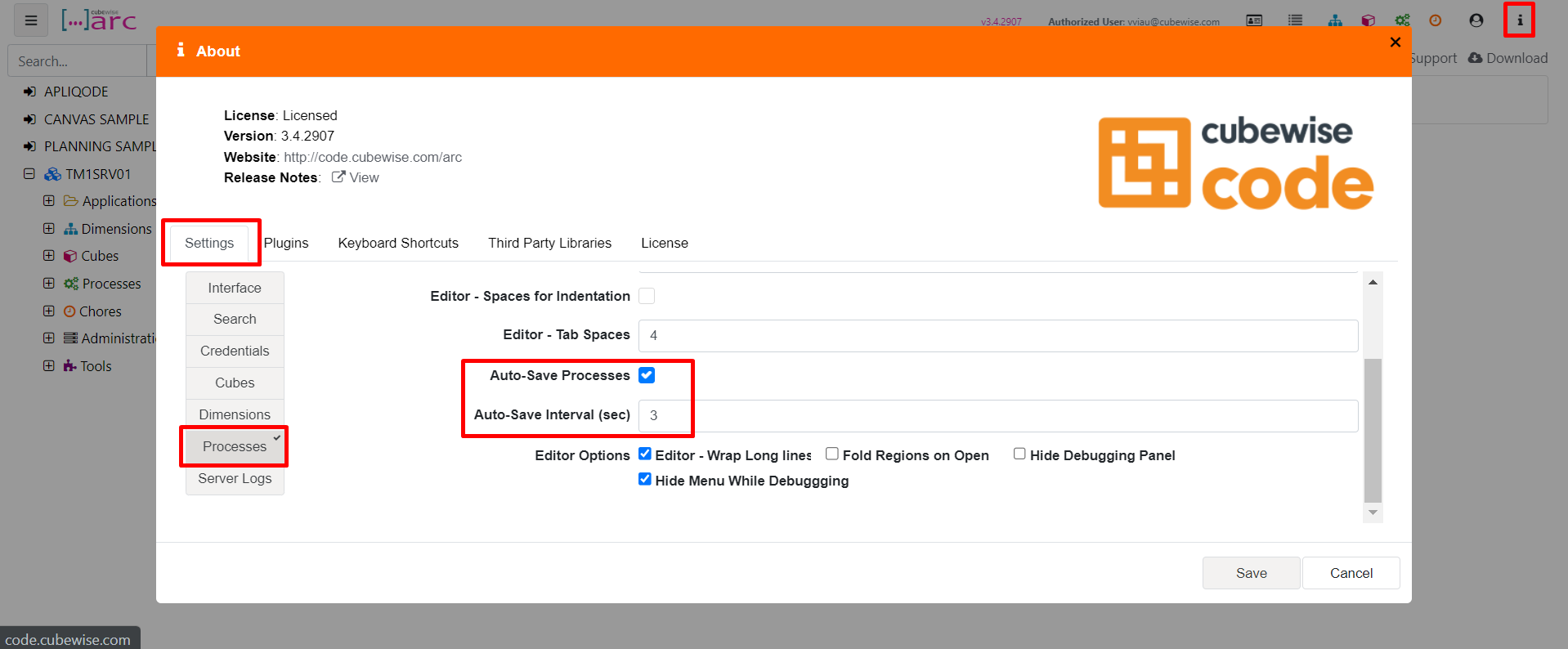
Starting with Arc v3.4, Arc can now auto-save your process at a specific interval. This is handy to avoid losing your code if you get an internet connection issue.
-
Connecting Pulse to a PA SaaS instance with the non-interactive account
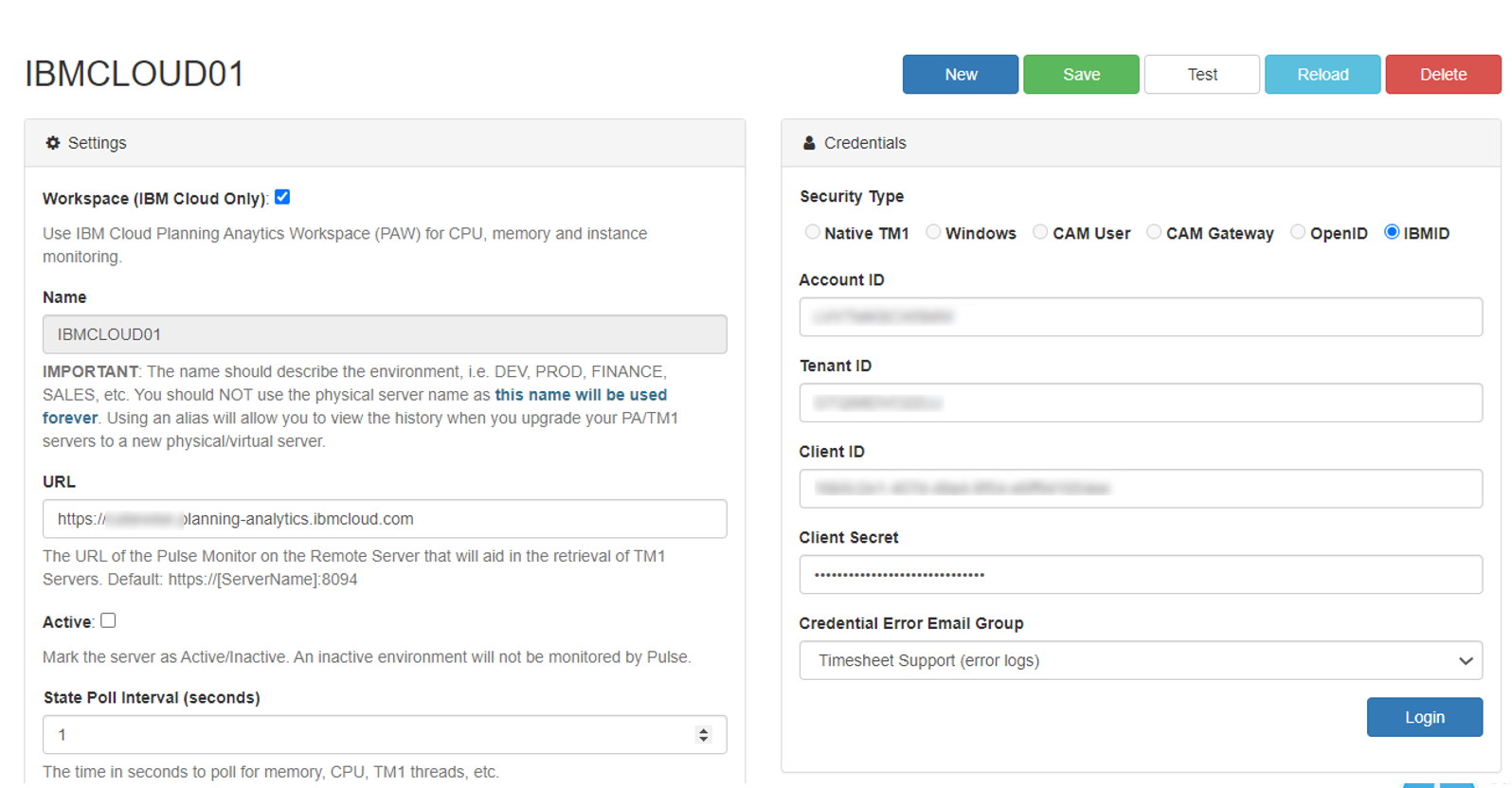
When Pulse is connected to a PA SaaS environment as the one below, you have to click the Login button and enter an IBM ID who has Admin access to PAW and to the TM1 instances:
-
Enabling TLS protocols in Arc
# Use only TLS protocols (v1.2+) and ciphers that are known to be secure
-
log4j Exploit – Possible Action Required

There has been a recent discovery of an exploit in the commonly used log4j library. The vulnerability impacts versions from 2.0 to 2.14.1. The vulnerability allows an attacker to execute remote code, it should therefore be considered serious.
-
Arc features comparison table (On-Premise vs IBM PA SaaS)
Arc can connect to many IBM Planning Analytics (TM1) instances: TM1 can be self-hosted (on-premise or on your private cloud such as AWS, Google Cloud… or on IBM PA Cloud (Planning Analytics Software as a Service).
-
Using Arc when TM1 instances are hosted on the IBM Cloud SaaS
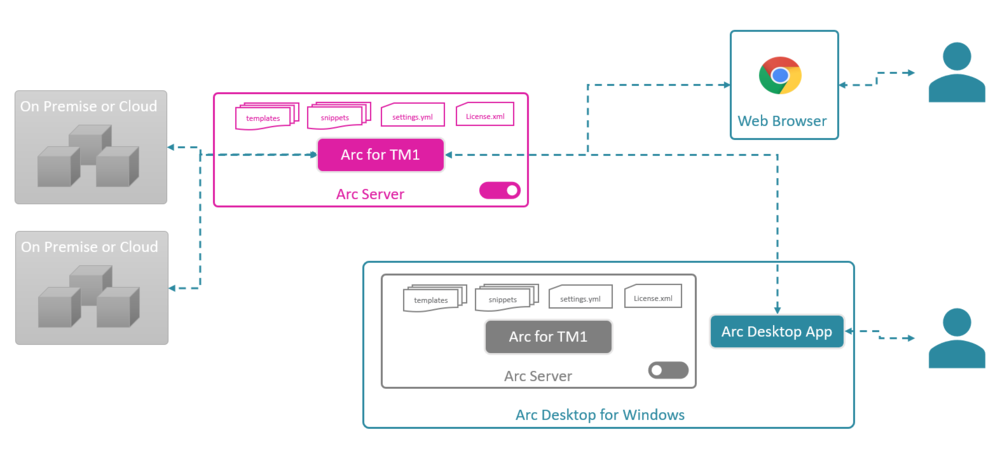
This article explains the different ways of using Arc when IBM Planning Analytics (TM1) instances are hosted on the IBM Cloud SaaS.
-
Using IBM ID with Arc
When your IBM Planning Analytics (TM1) instances are hosted in the IBM Cloud SaaS (PA SaaS), you can use your IBM ID credentials with Arc.
-
Grouping TM1 servers and instances in Arc
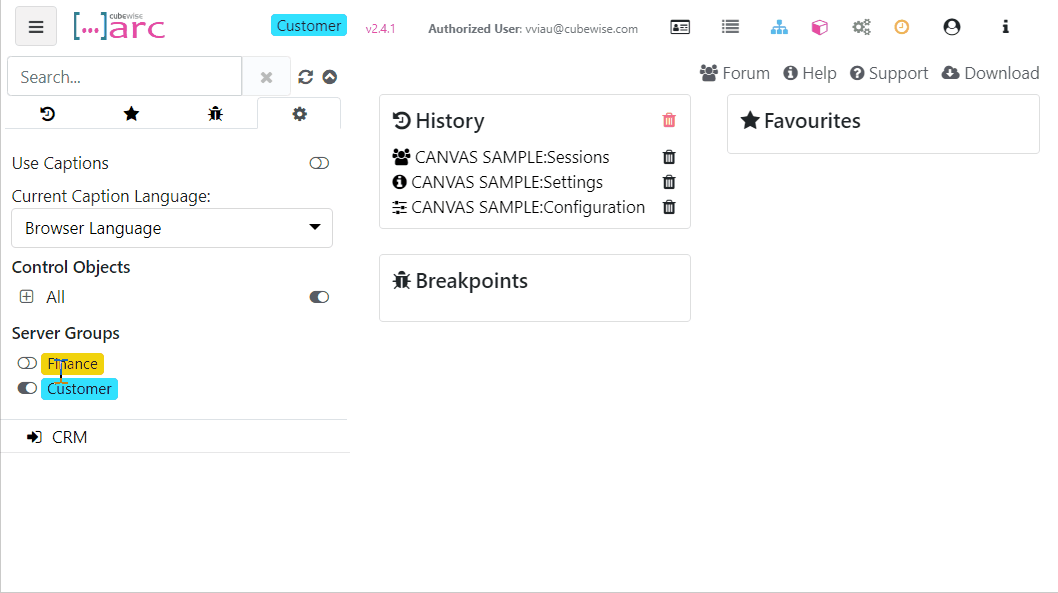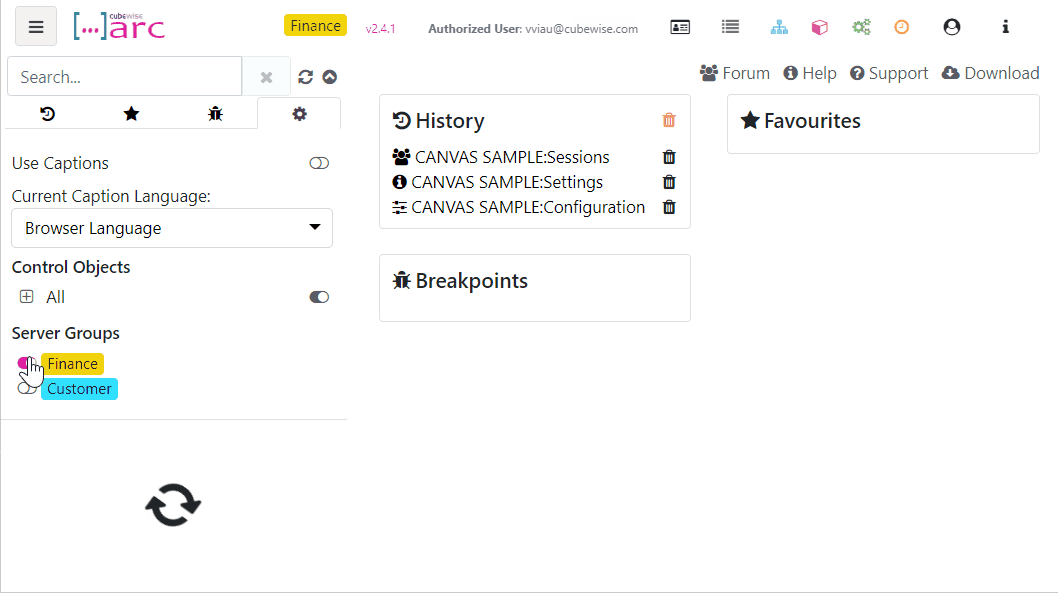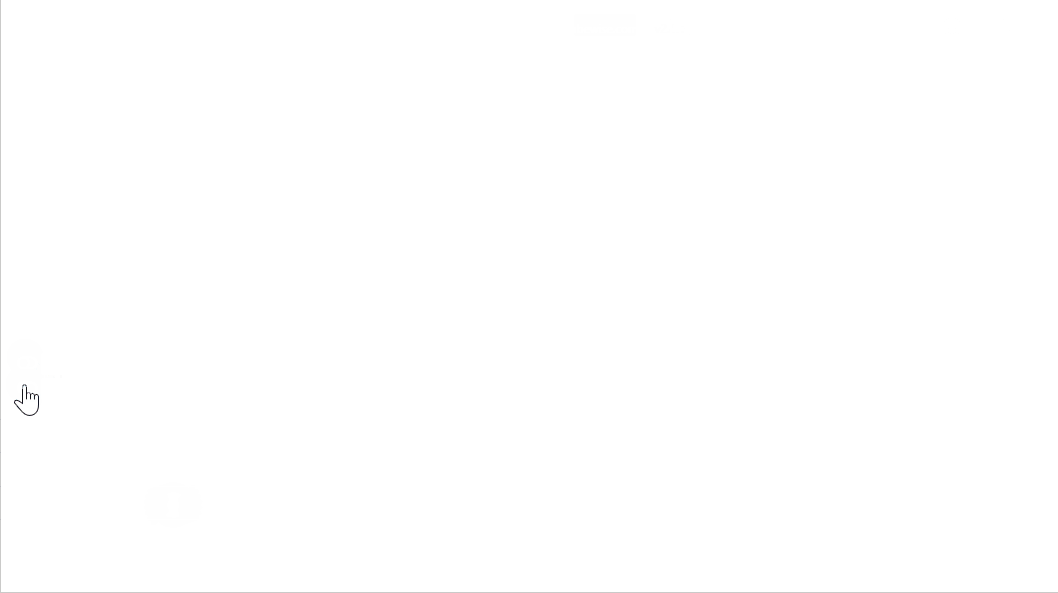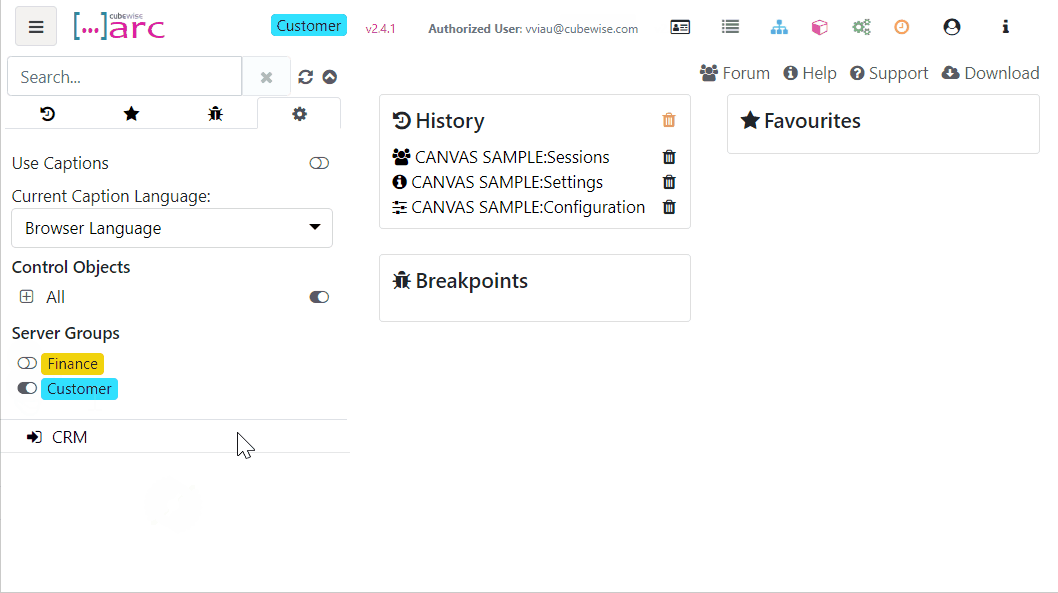
Starting with Arc v2.4, we have added additional support for multiple admin hosts and connections so you can group them together and toggle between the groups, we have called them Server Groups. This is targeted at environments that have many admin hosts and connections: